
How to Modify a Hermes React Native Application
Before you start reading, this article isn’t about decompiling and modifying the Hermes code. Instead, it aims to change the communication between the React and OS Native sides.
Hermes is a software that compiles the JS code and turns it into bytecode; similar to Java and other languages that rely on bytecode mechanics. It is the engine that is specifically designed to be used with React Native. Because it supports bytecode compilation, it also performs static optimizations on JavaScript code. This is great for developers using Hermes because their code will be harder to decompile back to it’s original state. Another fact about Hermes is that it changes the bytecode interpretation and compilation slightly with each new version, so it will be even harder to decompile a Hermes-compiled piece of software.
You know, we have the Hermes engine source code open source on GitHub. This is not a case of security over obsolescence. So we also have all of the versions’ code responsible for bytecode compilation and optimization. So why can’t we revert the bytecode compiled source back to its original state? Because even though we have the compilation code, we also need a decompilation code. At the time I’m writing this, there are two projects exist on GitHub that decompile and parse Hermes-compiled software. However, they don’t have support for Hermes v90, which is the version I’m working on. So Hermes is somewhat secure.
After all this Hermes-related briefing, I would like to present how I managed to break it in a different way. My goal was to break/change some of the functionality in a pentestiation application so that it would start working the way I wanted it to. It’s my device and I decide how it works, right?
The way all of the React Native apps work is that they have layers of software. For Android there are 3 layers.
1) Native where C/C++ is used
2) Java
3) React Native application code (usually JavaScript, in this case Hermes bytecode)
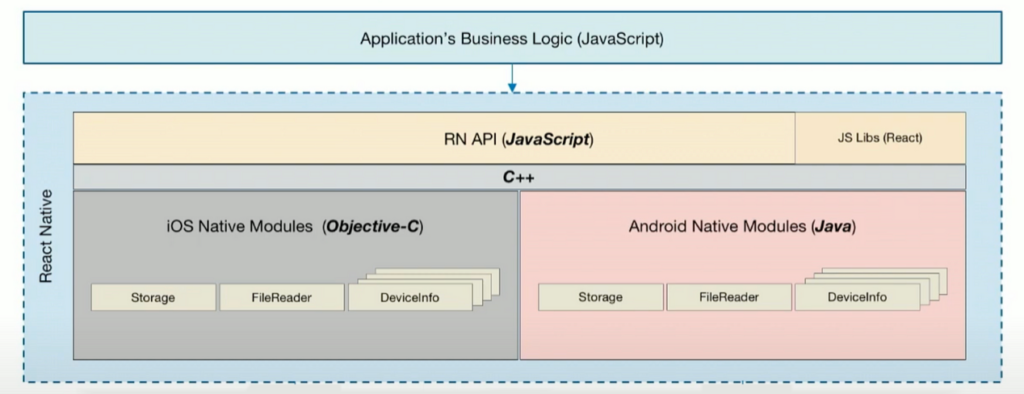
The image is from an article by Shihara Dilshan.
The bridge between the React Native application and the Android operating system is maintained by the Native and Java code. These are the languages that Android knows and works with. So while the Hermes bytecode implementation will protect the application quite well, there are still some open windows. Because React Native still needs to use OS-specific functions, it is very possible to manipulate the communication between the React Native application and the OS-dependent Java code. And Java is a very fundamental part of Android, so there are always tools available to decompile, modify, and then even recompile it.
So that is what I did. I extracted the libraries from the plain text modules.json file that exists in React Native applications, whether they use Hermes or not. What I found out is that most of the libraries that are used in the application are open source. I can literally go and read what it does in the operating system to work and what methods it uses to communicate with React. I override some of the methods with NOP because I want them to remain passive even if React sends them a command. It is also very easy to return overridden values.
After all that, the plan had worked as expected. I disabled proxy block in the application and then trusted it to my proxy’s SSL certificate. Well, proxy should be the biggest nightmare of any developer relying on a network. And because the React application has to communicate with the Android OS to ask if a proxy is currently being used, it is possible to disable it this way. I then used the proxy to extract the application’s API. With the application’s API in hand, it is possible to perform a penetration on the API, which is more business critical. It is even possible to build your version of the application with the API (something I have done before).
However, in this case, the application I have done these things with is already an open source application that is made for a challenge. The app’s owner deliberately designed the app to be pentestable.
I would strongly advise my readers to be responsible and smart. Penetration can be like playing chess. It is not like a brute force. It is something that is done with knowledge and experience. Please use your strength to advance the humanity. Not to damage the things they build. This article was written for educational purposes only.
Next





Comments are closed